These days, data is everything for businesses. Whether it’s customer information or financial records, companies depend on sensitive data to keep operations running smoothly and provide great service. However, with cybersecurity threats on the rise and strict privacy laws in place, protecting that data has become a top priority.
Data masking ensures that data remains secure and private, regardless of circumstances. This is where data masking emerges as a critical solution, rapidly becoming a non-negotiable necessity for organizations of all sizes.
The Critical Role of Data Masking in Modern Enterprises
The past few years have witnessed a surge in high-profile data breaches, with cybercriminals employing increasingly sophisticated tactics to infiltrate corporate networks and access sensitive information. The consequences of such breaches can be catastrophic, resulting in financial losses, reputational damage, and erosion of customer trust.
According to a recent study, the global average cost of a data breach reached a staggering $4.35 million in 2022, with the industry experiencing the highest average cost of $10.10 million per breach.
Data Privacy Regulations Compliance
In response to the growing concerns over data privacy and security, governments worldwide have introduced stringent regulations to protect consumer data. The General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) are prime examples of such legislation.
The GDPR has resulted in over €1.5 billion in fines since its implementation in 2018, while the CCPA has imposed $1.2 million in fines and settlements as of 2022. Failing to comply with these regulations can result in severe penalties and damage to a company’s reputation.
Data masking is no longer an option, it’s a necessity. Increasing cybersecurity threats and regulatory demands have made prioritizing robust data protection measures imperative for businesses.
Key Drivers of Data Masking Adoption
Protecting Sensitive Customer Data
Data masking has become a non-negotiable practice for today’s businesses due to the increasing need to safeguard sensitive information while maintaining usability. But what does masking mean? In essence, data masking involves the transformation of data to conceal its original values, thus protecting sensitive information such as personally identifiable information (PII), financial data, and intellectual property.
Safeguarding sensitive customer data is a top priority for businesses across various industries. In the financial sector, data masking plays a crucial role in protecting sensitive financial information and ensuring compliance with regulations such as PCI DSS. The average cost of a financial data breach is a staggering $5.72 million per incident.
Similarly, the healthcare industry faces the highest average cost of a data breach, at $10.10 million per incident, underscoring the need for robust data masking solutions to protect patient records and comply with HIPAA regulations.
E-commerce businesses must also prioritize data masking to secure customer data and adhere to PCI compliance, as the average cost of a PCI DSS non-compliance penalty ranges from $5,000 to $100,000 per month.
Secure Data Sharing in Development and Testing
Effective software development and testing often require access to real-world data, potentially exposing sensitive information to unnecessary risk. Data masking plays a vital role in addressing this challenge by providing anonymized realistic data for development and testing purposes.
Many organizations use production data for testing and development, exposing sensitive information to potential breaches and compliance violations. Data masking ensures secure data sharing without compromising privacy or data integrity.
Insider Threat Mitigation
While external cybersecurity threats garner significant attention, businesses must also address the risks posed by internal users with access to sensitive data. Data masking minimizes these risks by obscuring sensitive information within reports, queries, and business intelligence tools, reducing the likelihood of accidental or malicious data exposure.
Data Masking Implementation Strategies
Effective data masking implementation requires careful consideration of various strategies and techniques tailored to an organization’s specific needs and data environments.
Static vs. Dynamic Data Masking
- Static Data Masking: This approach involves masking data within non-production environments, such as development, testing, and analytics platforms. Static masking is widely adopted, with 68% of organizations utilizing this method to protect sensitive data during application development and testing cycles.
- Dynamic Data Masking: Unlike static masking, dynamic data masking occurs in real-time within production environments. This approach ensures that sensitive data is masked on the fly as it is accessed or queried, providing an additional layer of protection for live systems. 32% of organizations currently employ dynamic data masking solutions.
Role-based Access Control (RBAC)”
Implementing data masking in conjunction with Role-Based Access Control (RBAC) is a best practice for ensuring the principle of least privilege. By aligning data masking policies with role-based permissions, organizations can ensure that only authorized individuals have access to sensitive data based on their specific job responsibilities.
Studies show that RBAC can reduce the risk of data breaches by up to 45%, highlighting its effectiveness in mitigating insider threats.
IT Automation and Orchestration
As data environments become increasingly complex, with data residing in databases, files, and data lakes, automating data masking processes is essential for efficient and consistent implementation. Automated masking tools and workflows streamline the process, reducing the risk of human error and ensuring seamless integration with existing data management systems.
60% of organizations plan to increase their investment in data masking automation tools, recognizing the benefits of streamlined and scalable data protection strategies.
Business Benefits of Effective Data Masking
Implementing effective data masking solutions not only mitigates risks but also delivers tangible business benefits that contribute to long-term success and profitability.
- Enhanced Data Security and Privacy
By masking sensitive information, businesses can significantly reduce the risk of data breaches and improve overall data security posture. Companies that fully deploy data masking solutions can potentially reduce the cost of a data breach by up to $1.5 million, according to industry estimates.
- Regulatory Compliance and Reduced Legal Risks
Data masking plays a crucial role in ensuring compliance with various data privacy regulations, such as GDPR, CCPA, and HIPAA. Failure to comply can result in severe penalties, with the average cost of non-compliance penalties ranging from $100,000 to $1 million per violation. Implementing robust data masking solutions minimizes the risk of regulatory fines and legal liabilities.
- Increased Customer Trust and Brand Reputation
In today’s digital age, consumer trust is a valuable commodity. 81% of consumers state that they will not do business with companies they do not trust to protect their data. By demonstrating a strong commitment to data protection through effective data masking practices, businesses can reinforce customer confidence and maintain a positive brand reputation.
Emerging Trends in Data Masking Technologies
The data masking landscape is constantly evolving, with new technologies and approaches emerging to address the challenges of modern data environments.
AI-Driven Masking Algorithms
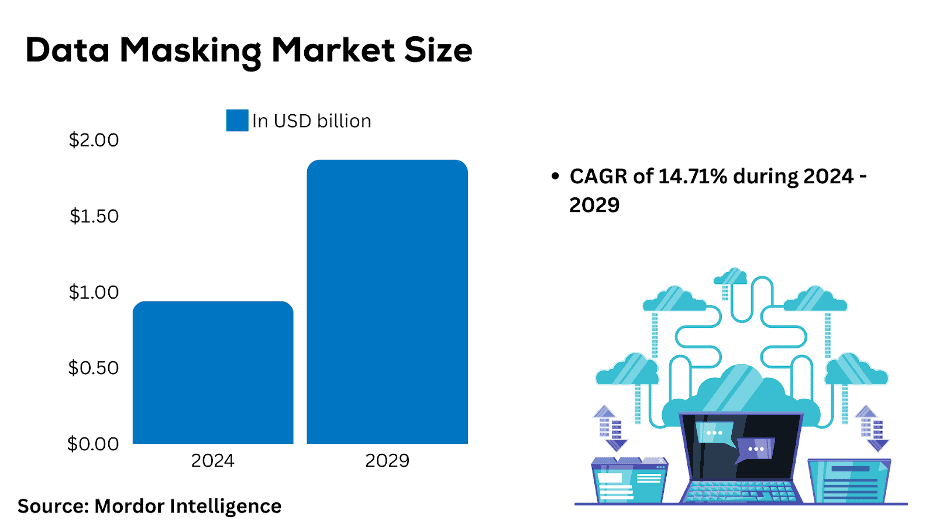
Utilizing artificial intelligence (AI) and machine learning (ML) algorithms for data masking is a rapidly growing trend. These advanced techniques can accurately identify sensitive data patterns and apply intelligent masking techniques, reducing the risk of accidentally exposing sensitive information. The global AI in data masking market is expected to grow from $0.94 billion in 2024 to $1.87 billion by 2029, at a CAGR of 14.7%.
Data Masking in Cloud and Hybrid Environments
As businesses increasingly adopt cloud computing and hybrid IT infrastructures, the need for cloud-native data masking solutions has become paramount. These solutions address the unique challenges posed by multi-cloud environments, ensuring consistent data protection across diverse platforms and locations. With 92% of enterprises having a multi-cloud strategy, the demand for robust cloud-based data masking solutions is set to rise.
Privacy Enhancing Technologies (PETs)
Data masking is increasingly being integrated with other Privacy Enhancing Technologies (PETs), such as homomorphic encryption and differential privacy. These advanced techniques complement data masking by providing additional layers of protection and ensuring data privacy throughout the data lifecycle. The global PETs market is expected to grow from $0.3 billion in 2022 to $1.4 billion by 2027, at a CAGR of 35.2%.
Embrace Data Masking as a Non-Negotiable Necessity
As data environments continue to evolve and become more complex, businesses must stay ahead of the curve by adopting emerging technologies such as AI-driven masking algorithms, cloud-native solutions, and privacy-enhancing technologies. By doing so, they can future-proof their data protection strategies and maintain a competitive edge.
Don’t wait until a costly data breach or regulatory fine forces your hand. Prioritize data masking as an integral component of your overall data security and privacy strategy. Invest in the right technologies, implement best practices, and embrace data masking as a crucial step towards safeguarding your most valuable assets, your data, and your customers’ trust.
Take the first step towards enhancing your data protection posture by scheduling a consultation with our data masking experts. Together, we can assess your specific needs and develop a data masking strategy that aligns with your business objectives and regulatory requirements.